Sam wants to send secret messages to Sally, and visa versa, so they
devise a simple but effective encryption scheme they can perform by hand.
However, they soon begin to fall in love and their messages to each other
are growing longer and longer. Therefore, they decide their encryption scheme
needs to be automated. Your job is to write a computer program that will
implement their "shake, rattle and roll" encryption scheme. (Decryption will
not be implemented at this time.)
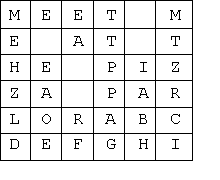
A text message is placed into a 2D array in row major order, with each
character in a unique cell of the array. If the message does not totally
fill the array, the empty cells are filled with the capital letters of the
alphabet starting with the letter A and going thru the letter Z (repeated
as needed). For example, the message, "Meet me at the pizza parlor" in a
6 by 6 array would look like the figure below. Note that all characters are
stored as capital letters.
To encrypt this message, 3 separate operations are performed as follows:
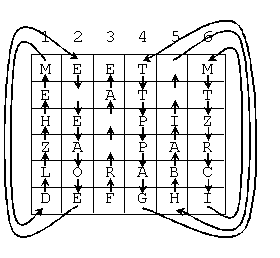
Shake: Each odd column is shifted up one character, with the top
most character moving to the bottom of the column. Each even column is shifted
down, with the bottom most chararacter moving to the top of the column. The
columns are numbered starting at 1. For example:
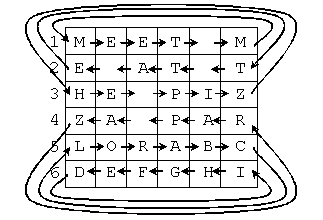
Rattle: Each odd row is shifted to the right one character, with
the rightmost character moving to the leftmost column in the same row. Each
even row is shifted to the left one character, with the leftmost character
moving to the rightmost column in the same row. The rows are numbered starting
at 1 from the top. For example:
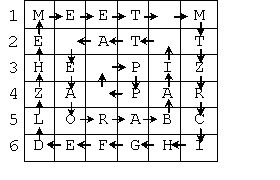
Roll: Each odd "loop" around the matrix is rotated to the right
one character, while each even "loop" is rotated to the left one character,
as shown in the figure below. "Loops" are even or odd based on the row number
of their top most row (with the top row being row 1).
The matrix size is specified in the encryption key and can vary in size from
3x3 to 100x100. The matrix is always square.